
What is a HoneyPot in Telegram and how to recognize scammers?
We tell you how newcomers to cryptocurrency are scammed with the help of a HoneyPot in Telegram. How to recognize scam and avoid manipulation by scammers.
Unfortunately, the cryptocurrency industry has become fertile ground for HoneyPot schemes. Unscrupulous market participants deftly play on FOMO and the greed of users who want to benefit from investments as soon as possible.
Telegram has become an excellent platform for launching all kinds of cryptocurrency mini-games and applications recently. Interacting with the Web3 world has become even easier, but not safer. Taking advantage of the sense of trust in such a large-scale site, the scammers moved the HoneyPot scheme here.
Before understanding how a simple messenger user can recognize and protect themselves from a HoneyPot in Telegram, let's look at what this scheme is.
What is a HoneyPot?
A HoneyPot or a "bait" is not a new fraud scheme, however, with the advent of new trends in the crypto market, this scheme adapts to them and, unfortunately, it becomes more difficult to track it. Its essence lies in the fact that intruders extort funds from gullible users.
Attackers create projects, promote them among users with promises of incredible financial benefits, and then disappear with users' funds. For example, more inexperienced users are lured by the idea of simple mechanics of a particular project. Advanced users would immediately pay attention to the main principles of cryptocurrency projects and conduct their own analysis before diving into the project and giving it their funds.
Simply put, with such a scheme, it is important for scammers to create an attractive offer that looks legitimate and safe and encourage victims to agree to this offer.
All kinds of psychological manipulations and pressure are the main principle of operation of the HoneyPot, which users should pay attention to in order to avoid it.

Where are the HoneyPot schemes hiding?
There are several main areas in the crypto industry where scammers deploy a scam scheme, and which the average user should pay attention to. One of the most popular is the creation and use of fake smart contracts and dApps. At first glance, they look quite legitimate. Such a smart contract or decentralized application promises high profitability or participation in the game, farming, mining for a reward. However, they contain bugs or other vulnerabilities in their code. The vulnerability is a fallback exit for scammers, through which they slip away unnoticed with user funds.
Some scammers create fake investment platforms instead of smart contracts. They may well look like ordinary exchanges or funds. And they can even work legally for a while and bring investors what they came for. So, the attackers are trying to instill imaginary trust. But at some point, fraudulent exchanges and platforms disappear with the funds of deceived users.
Airdrop remains one of the most popular events in the cryptocurrency field. This is a completely normal way for newly launched projects to attract more users. However, scammers have learned to apply the HoneyPot scheme in this direction as well.
The same principle applies here - to lure victims with promises of financial gain. The user sends funds to the scammer in the hope that he will receive more tokens in the future. Therefore, it is important to pay attention to the transparency and accountability of airdrop projects. Airdrop conditions should also be transparent.
This method is one of the most common today. Most often, scammers are popular with new projects that are about to release their token and airdrop it among the community. The attackers launch a fake project token and announce its airdrop. Users connect their wallets and eventually lose their funds. Here, it is important for the user to follow the official social media pages of the project and carefully check the address of each link.
Phishing is also part of the HoneyPot scheme. Fake websites of well-known exchanges and platforms are being created that look exactly like the real ones. With the help of e-mail newsletters or other communication channels, scammers are encouraged to click on the link and connect the wallet. This way, attackers gain access to the victim's wallet. There is no need to follow links from unfamiliar users and projects.
Scammers also like to place baits on decentralized exchanges. They create trading pairs with a non-existent token. When users exchange their real tokens for fake ones, they lose funds. Careful behavior with little-known projects/tokens is part of digital hygiene.
How do scammers implement HoneyPot in Telegram?
As mentioned above, it is important for unscrupulous market participants to gain the trust of users. To do this, they create a thematic Telegram channel, promote it through built-in advertising functions, and gain several tens of thousands of subscribers. For a while they publish quite working content, aggressively advertise their channel. Unfortunately, the popularity and trust in Telegram plays into the hands of scammers. This creates a false sense of security. Below we will talk about how an ordinary user can recognize a scam channel.
Further, this scheme acquires several options for the development of events. The scammers are quietly planting a mousetrap. Since mini-games have made a real splash in the messenger now, nothing prevents attackers from "launching" their own. They promote their product, promise to launch a game token and ask to connect their wallets for distribution as soon as possible. Next, they get access to the wallet and drain all the user's funds from there. If you are not sure about the project, you should not connect a wallet to it.
There is another option. After the scammers have gathered the right audience on their channel, they create a copy of it with the same number of subscribers in the form of bots. Next, the scammers give the username of the channel with a live audience to the channel with bots. A fake token/project appears on the "live" channel, which lures funds from victims. This channel is also being transferred to the closed status. A complaint about a scam from a user now arrives on the channel with bots. Support can ignore these complaints, since there is no scam in the channel with bots as a result. And unfortunately, this is a security flaw in Telegram, which is used by hackers.
Here is an example of HoneyPot schemes. Pay attention to how the manipulations of scammers can look like in order not to fall for them:
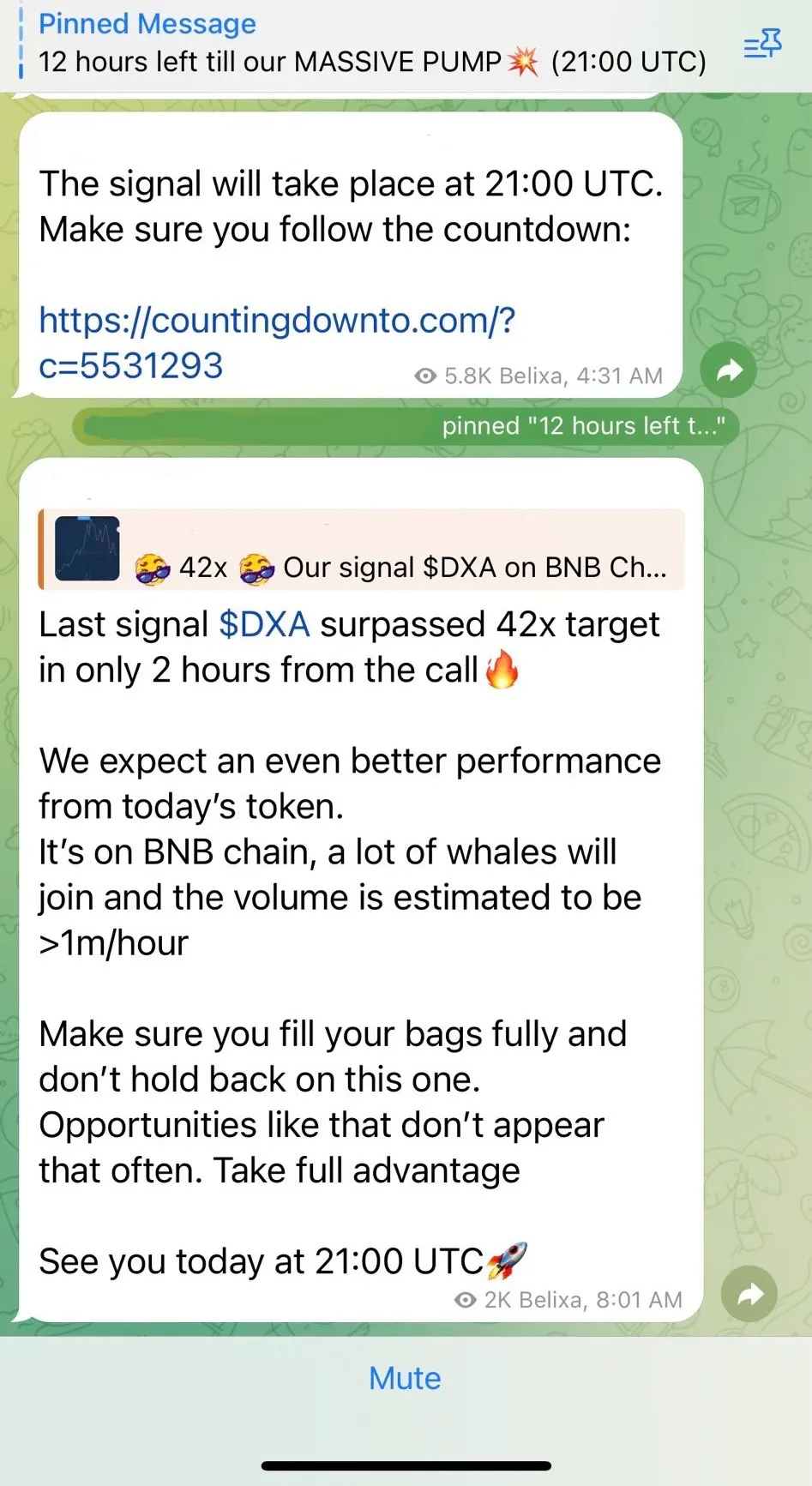
How to protect yourself from a HoneyPot
Remember that the primary task for a scammer in implementing a HoneyPot scheme is to gain the trust of users. They will spend their time and energy on this. They will probably initially play by the rules, draw a portrait of an expert who should be trusted and even call for their own analysis, as well as behave with restraint with regard to calling for this or that action.
In this case, it is almost impossible for the user to distinguish a scam project from a legitimate one. And yet, the golden rule of conducting your own project analysis remains working.
Always check the authenticity of channels and accounts, especially when it comes to your money and personal information. Channels with a lack of reactions to posts and disabled comments are suspicious. Newly created channels and their admin pages are also alarm bells. Check the legitimacy of the project on third-party forums and communities. Projects should have a technical document, at least. Smart contracts of such projects must undergo a security audit. So be sure to pay attention to this aspect as well.
Do not click on suspicious links that may appear on the channel or in the comments under the posts. Do not share your data and go through the 2FA of your Telegram account.
Be wary of those projects that offer too high returns in a short time. And to protect against phishing, use an antivirus and special software. There is no absolute guarantee of protection against HoneyPot schemes. However, you can protect yourself as much as possible. Conduct your own analysis and learn to recognize potential scam projects.
Conclusion
There is no one hundred percent guarantee of protection against HoneyPot systems. However, the user can protect himself as much as possible. Conduct your own analysis and learn to identify potential scam projects. And if it does happen that you have been scammed, you should immediately contact the police and cybersecurity experts.
























